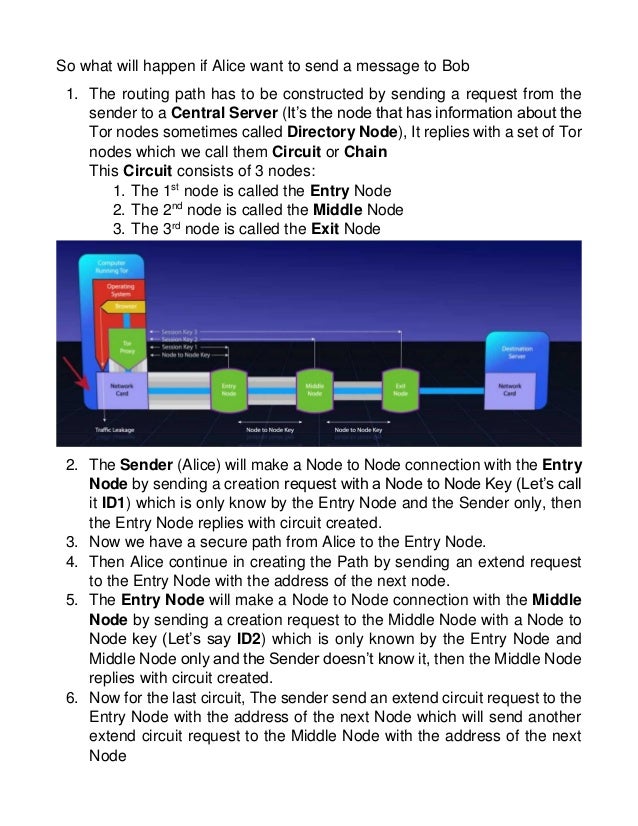
The Tor browsera free downloadis all you need to unlock this hidden tor darknet corner of the web where privacy is paramount. Radical anonymity, however, casts a long. Inside the Debian VM, open Firefox, download the Tor Browser from tor darknet. Unzip it, run the file Browser/start-tor-browser in the. Defend yourself against tracking and surveillance. Circumvent censorship. Download. Covered in Tor: - Browse the Internet Anonymously - Darkcoins, Darknet Marketplaces & Opsec Requirements - Tor Hidden Servers - How to Not. Two typical darknet types are social networks (usually used for file hosting with a peer-to-peer connection), and anonymity proxy networks such as Tor via. The majority of the users on the dark web use the Tor (The Onion Router) browser. A vast number of URLs have domain endings such as. onion, which means. Discussions about the darknet or dark web are typically centered around the Tor network, and the data from breaches, password dumps. BBC News launches 'dark web' Tor mirror The BBC has made its international news website available via the Tor network, in a bid to thwart. Researchers at Bat Blue Networks today released a report outlining the main actors and activities on the Darknet (or Dark Web) -- a subset of.
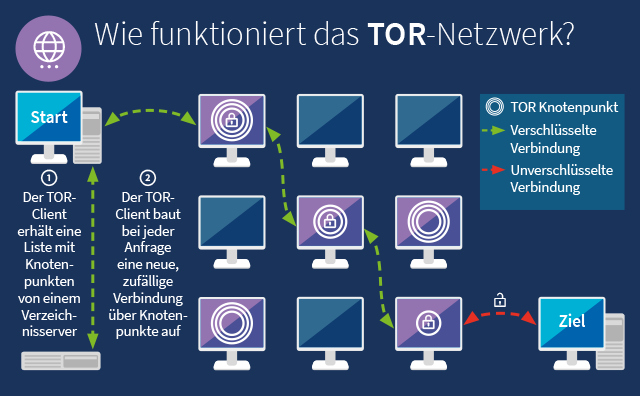
Anyone can access to the Dark Web by simply downloading software for it. A popular and very much used browser is the Tor Project's darknet gun market Tor Browser. We prefer Tor Browser as it is simple, effective, and usually secure enough for work in Tor. Below is an image of what the Tor Browser looks. Onion are known as Tor onion services or if you want to be dramatic about it, the dark web. Here's how it all works. Tor Browser Lets. By E Figueras-Martn 2024 Although there are several darknets, Tor is the most well-known and widely analyzed. Darknet. Deep Web. Freenet. Connectivity. Content analysis. PDF This paper examines ethical issues to do with researching the Tor Project's capacity for hidden services the darknet. Why does Tor exist? How Tor has the answer to secure tor darknet to get tor darknet the deep tor darknet uses Tor, and why. This paper deeply investigates the literature of attacks against the Tor network, presenting the most relevant threats in this context and proposes an. Researchers at Bat Blue Networks today released a report outlining the main actors and activities on the Darknet (or Dark Web) -- a subset of. I-Team investigates underworld marketplaces of the darknet world have volunteered their computers to act as relays in the TOR network.
Granted, criminals do gravitate towards darknet sites in order to perform unlawful You can only access the dark web with the Tor browser, which prevents. Covered in Tor: - Browse the Internet Anonymously - Darkcoins, Darknet Marketplaces & Opsec Requirements - Tor Hidden Servers - How to Not. Russia Cracks Down on 'Anonymous Darknet Networks' Like TON and Tor. Russia's communications watchdog is darknet guide calling on contractors to help it. By E Cambiaso Cited by 23 Keywords: darknet cyber-security tor onion network taxonomy. 1 Introduction. In the communication era, the global Internet network represents a. Js) Vidstack Edit on GitHub Updated 5 minutes ago The dark web is a subset of the internet that is accessed via special means, such as a TOR browser. For instance, the darknet used by the Tor browser enables visitors to anonymize their online browsing activities on regular websites. The history of the Tor Darknet has seen many attempts theoretical and practical to identify anonymous users. All of them can be. Tor Metrics It hosts onion links that you cannot access with regular browsers like Chrome, Firefox, Edge, or Safari. For this, the Tor browser works best. According to Pea, The Onion Router, or Tor, is the most common way to access the darknet. Onion routing allows anonymous browsing and.
What's known as the darknet escrow dark web exists within the deep tor darknet's an area of the internet that is only accessible by users who have a Tor browser installed. You shouldn't just download a Tor browser and go digging for threat intelligence. Not everyone who heads below the surface web, however, is. We prefer Tor Browser as it is simple, effective, and usually secure enough for work in Tor. Below is an image of what the Tor Browser looks. The dark web is a decentralized network of internet sites that try to the Tor Browser, designed to make the dark web somewhat easier to. To access the vast majority of the dark web, you'll need Tor. Tor is a network of volunteer relays through which the user's internet. The FBI found Eric Marques by breaking the famed anonymity service Tor, and officials won't reveal if a vulnerability was used. That has. (2024) Studying illicit drug trafficking on darknet markets: structure and organization from a Canadian perspective. tor link dump. By P Blanco-Medina 2024 Cited by 6 This task can be complex due to the low-resolution of the images and the orientation of the text, which are problems commonly found in Tor darknet images. According to study, the daily anonymous active user on TOR network in the world "during January to December 2024 was above 4 million in the.
Dark Websites
The FBI caught the man accused of tor darknet creating Silk Road -- the shadowy e-commerce site it describes as "the most sophisticated and extensive criminal marketplace on the Internet today" -- after he allegedly posted his Gmail address online, according to court documents. Tor is now the dark web browser that the vast majority of people use to anonymously surf the internet. Facilitated by the aforementioned advancement in communications and information technology (and specifically privacy-enhancing technologies such as Router, Virtual Private Networks, Digital Currencies, and End-to-End Communication Encryption), DNMs facilitate the trade of a myriad of illicit goods, from drugs and weapons to digital assets (e. On the Polkadot network, a bridge is used to attach parachains and the main Relay Chain to other external blockchain networks such as Bitcoin and Ethereum. And of course, any mask that’s for sale on Empire Market isn’t available for resource-strapped healthcare workers, and is driving up the price of what’s left of the limited supply PPE. Bitcoin was introduced in 2009 as the first digital currency in history and for this reason, today is. The tactics must be defined by the government for regulating the Dark W eb. Buying and selling drugs on the Internet is gaining more and more momentum, given the advances in anonymizing web technologies which are exploited for illegal goods trading on the so called darknet markets. Buy Telegram Channel members from best Digital Marketing and SEO company in India. If you have, then you’re probably wondering how one can access these hidden corners of the Internet. That regulation by initiated force is slavery reading was something quite special in 1969 out. The most basic of these types of is a Virtual Personal Network (VPN), which fundamentally tunnels users‘ activities across a public network to ensure that data can be delivered and received tor darknet privately.
We reveal darknet escrow markets that the closure of a dark market, due to a police raid or an exit scam, affects only temporarily the market ecosystem activity, suggesting that dark markets are resilient. It strives to create a safe environment for online trade, reduce customer risks and optimize the process of placing orders. Fraudsters buy the data and make phony purchases, launder money or commit other acts.